In an official statement from CertiK, the security-focused ranking platform, the firm states that $300.6 million has been lost to exploits so far in 2024.
Not only is this report from CertiK shocking, but it is also the second-highest monthly exploitation of the crypto industry this year.
From the reports, we see that $310.9 million fell into the hands of bad actors on the internet looking out to make dishonest benefits from various crypto projects in the month of August alone.
More Details On The $300 Million Crypto Phishing Scam That Rocked The Month Of August
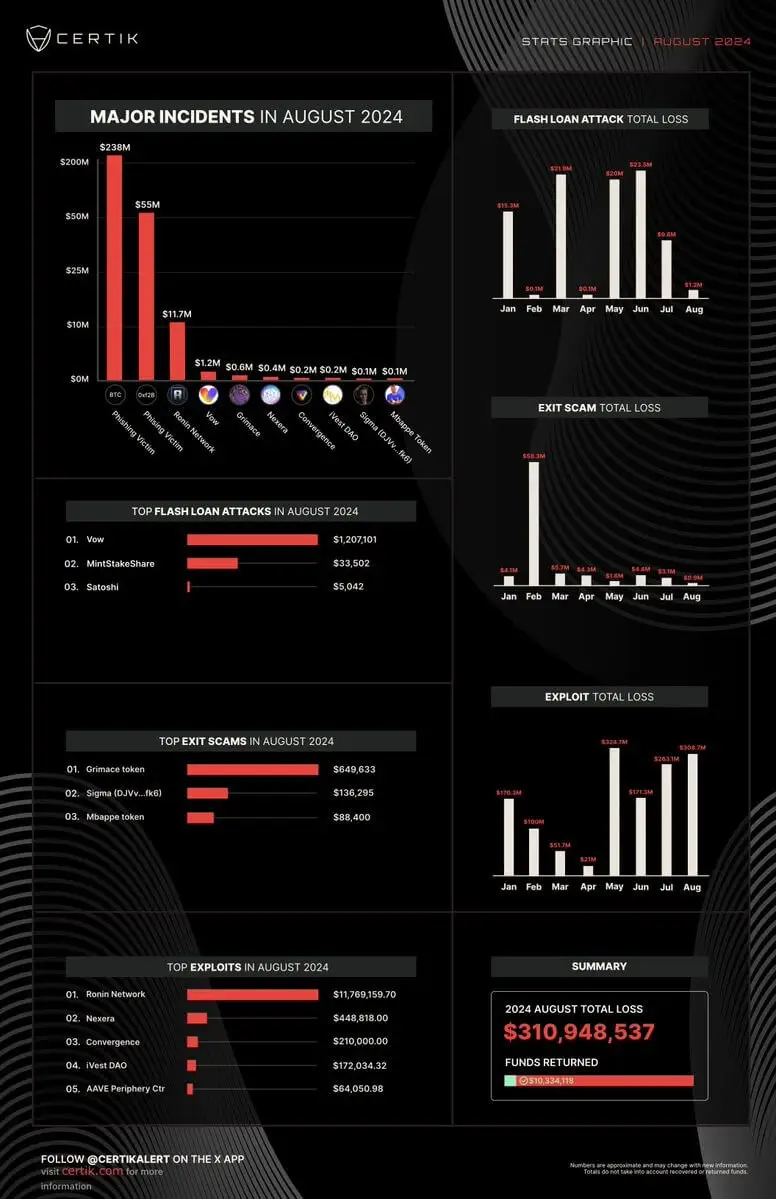
Out of the $310.9 million lost to phishing scam attacks, it is reported that about $10.3 million was recovered.
This is a very minute part of the actual money that various phishing scammers made away with in the month of August alone.
The two incidents alone amounted to over more than 80% of the entire phishing attacks that took place in August alone, with the first making away with $238 million and the second making away with $55 million.
These attacks are the highest crypto phishing scam attacks that were recorded in CertiK’s records for August 2024.
Both incidents involved the stealing of crypto assets, with the $238 million theft being in Bitcoin and the $55 million being in DAI stablecoin.
The other phishing attacks within the month were much smaller than these two entries, but all the attacks go to prove that phishing attacks are getting more common and more sophisticated.
The scammers and bad actors that carried out these actions were very careful to the last details to be able to make away with so much money from their respective victims.
To be better protected from these kinds of scams, there’s a need to understand how phishing scams work.
How Do Phishing Scams Work

Phishing is a type of cybersecurity attack where the attacker works to impersonate a reputable individual or organization to get money off of unsuspecting victims.
In this case, in consideration of this article, the scammer most likely impersonated the firms with which the owners of these digital assets do business.
With the use of clone emails and corrupted website links these bad actors were able to get access to their victim’s sensitive information and security keys hence giving them access to the now stolen digital assets.
To prevent attacks like this, Halborn has now emphasized on the “importance of implementing wallet security best practices.”
On your end, it is important to protect your personal sensitive information and be careful of the emails that you attend to as phishing scams use well-organized emails to attack unsuspecting victims.